Skip and Enforce Checks
To help you achieve security, compliance and quality of your automation while optimizing it, Steampunk Spotter allows you to centrally control which checks to enforce or skip across your Ansible Playbooks.Watch DEMO or read blog .
Organization Level
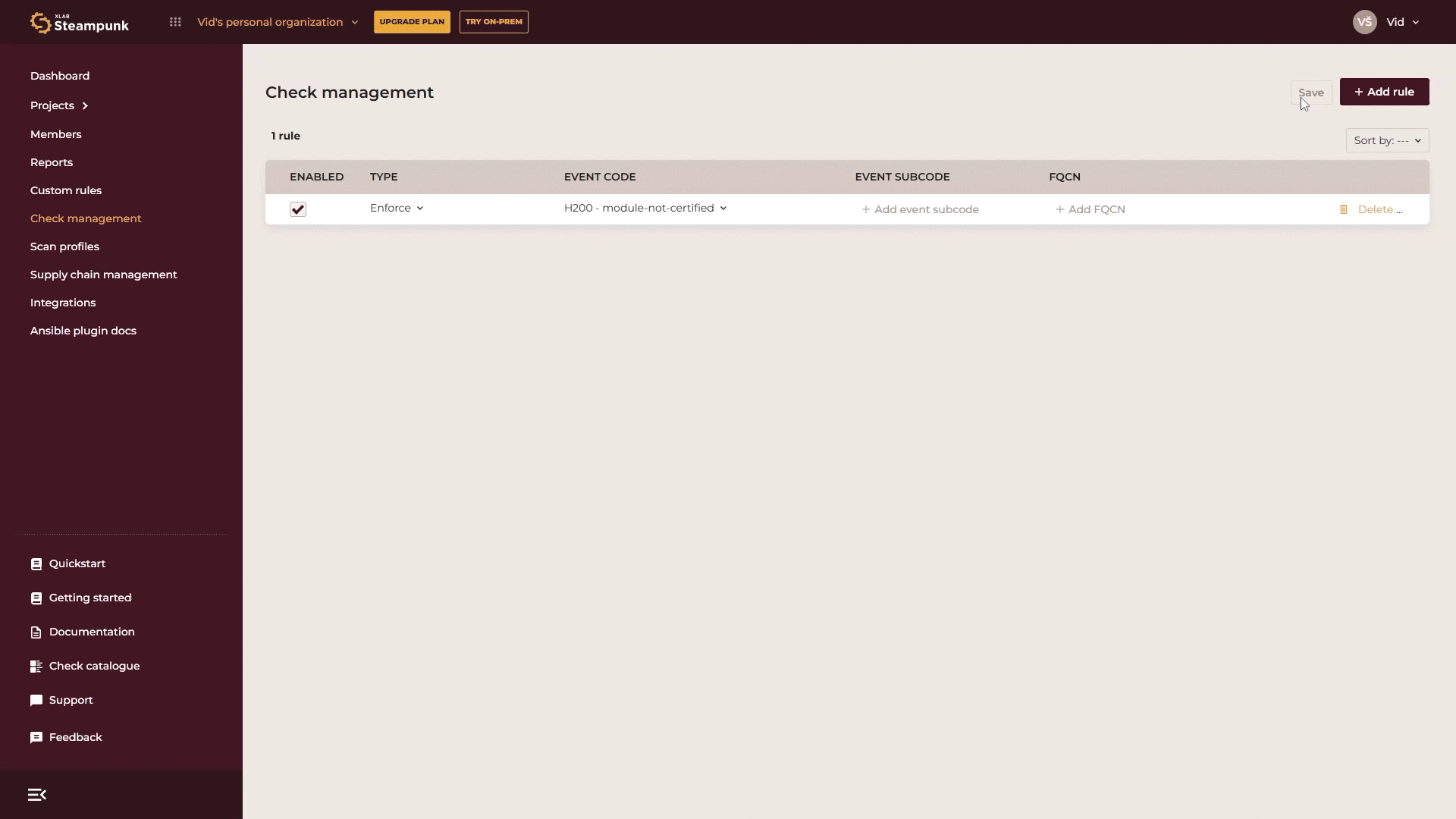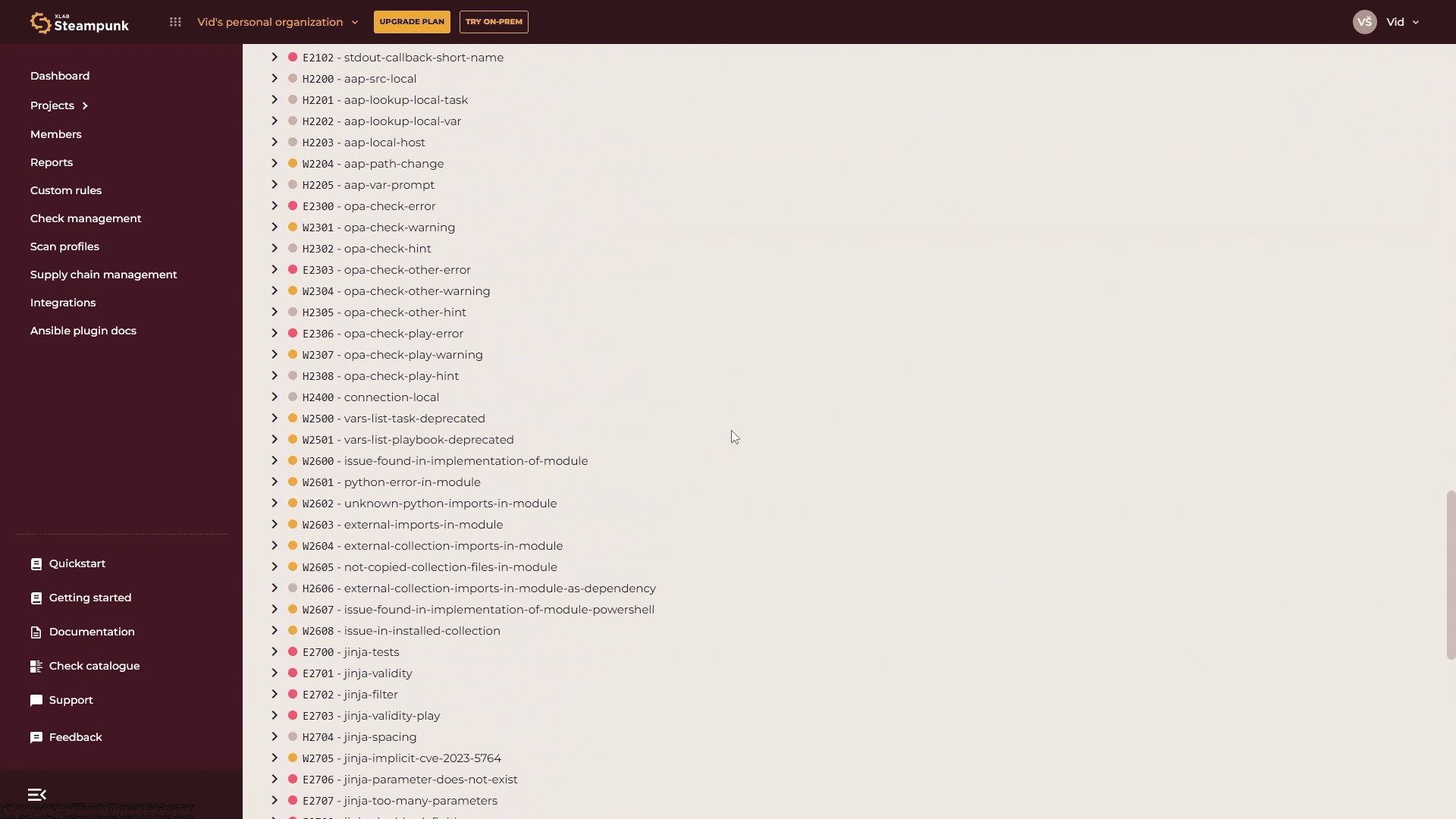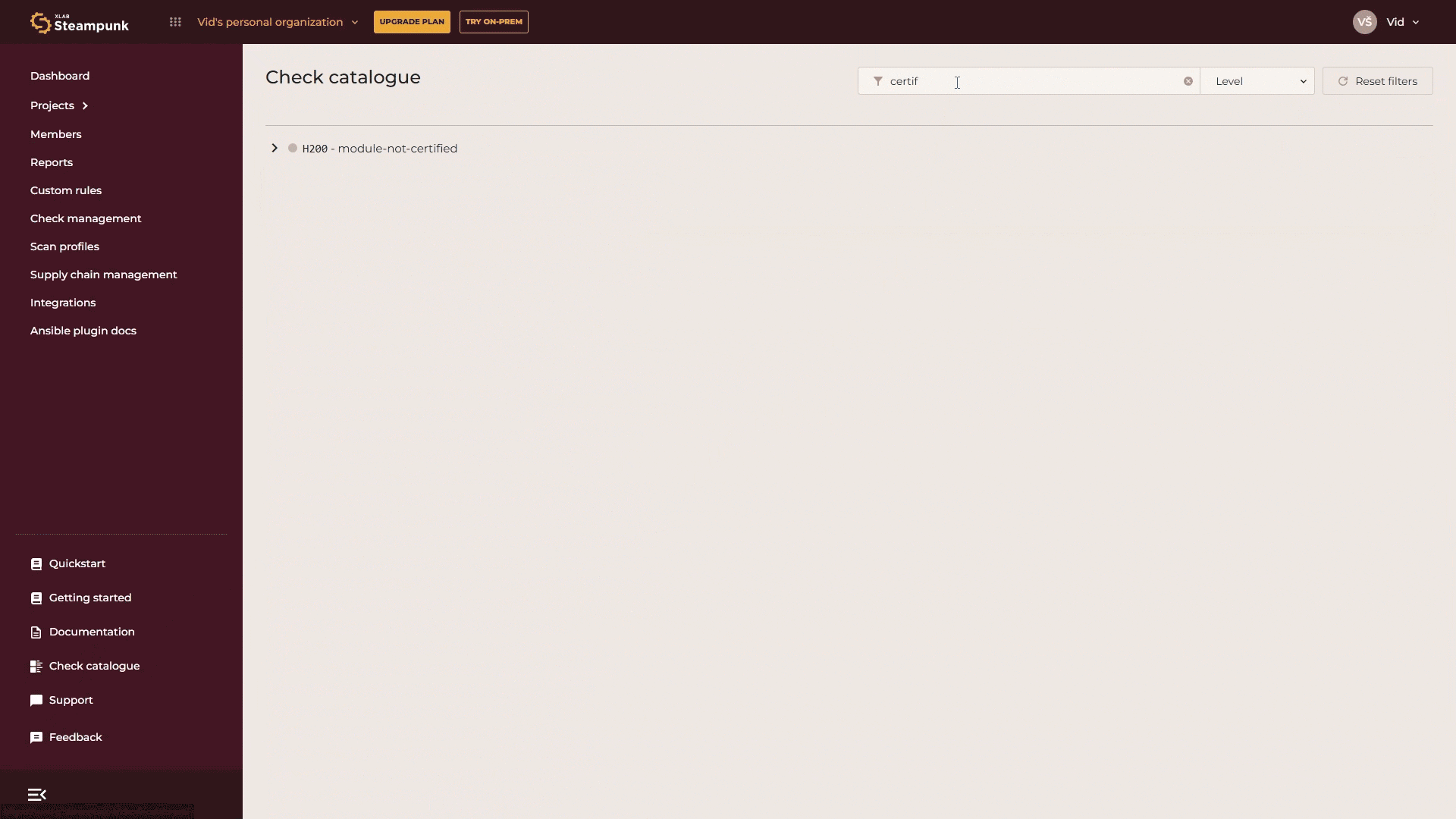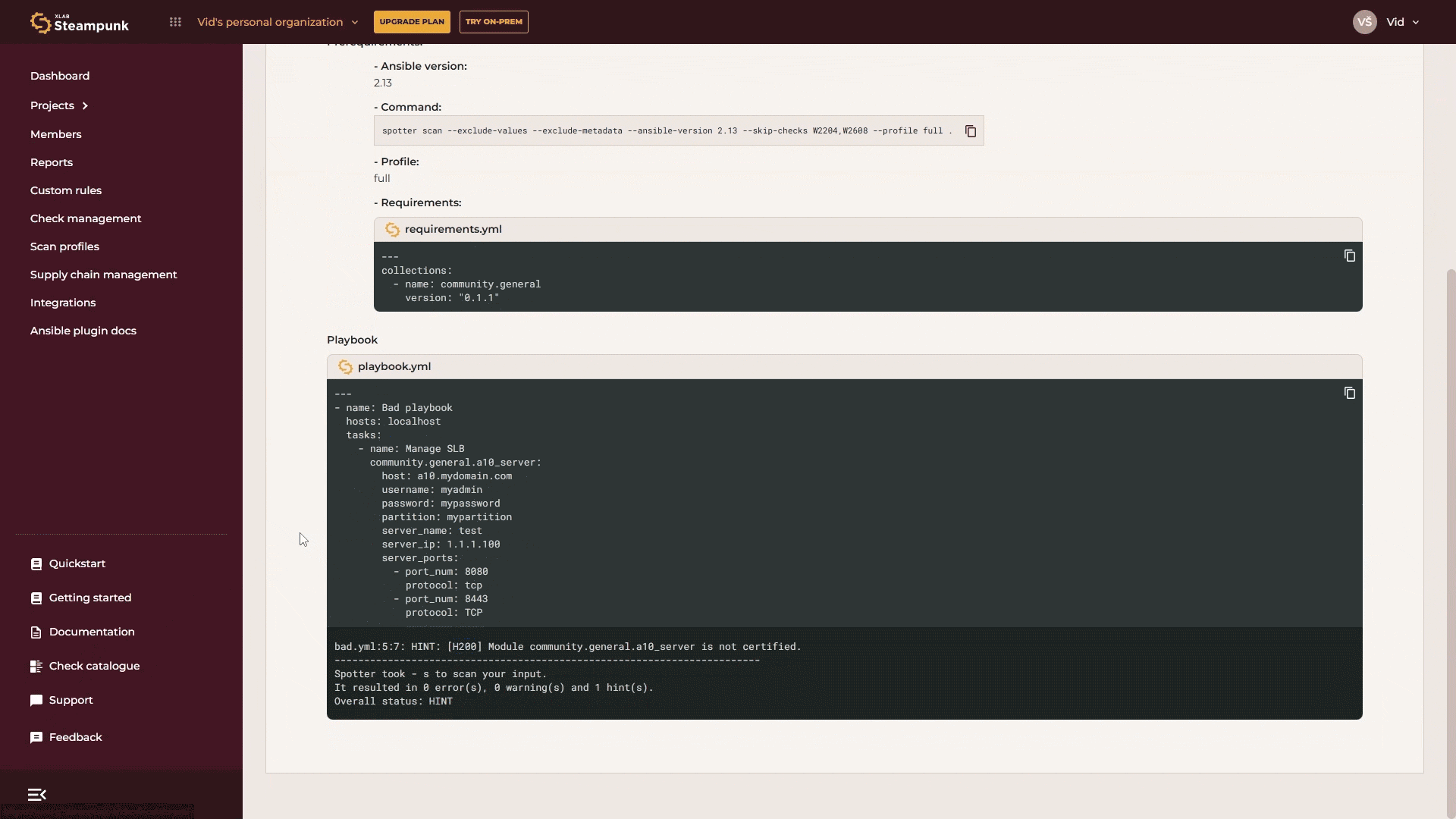
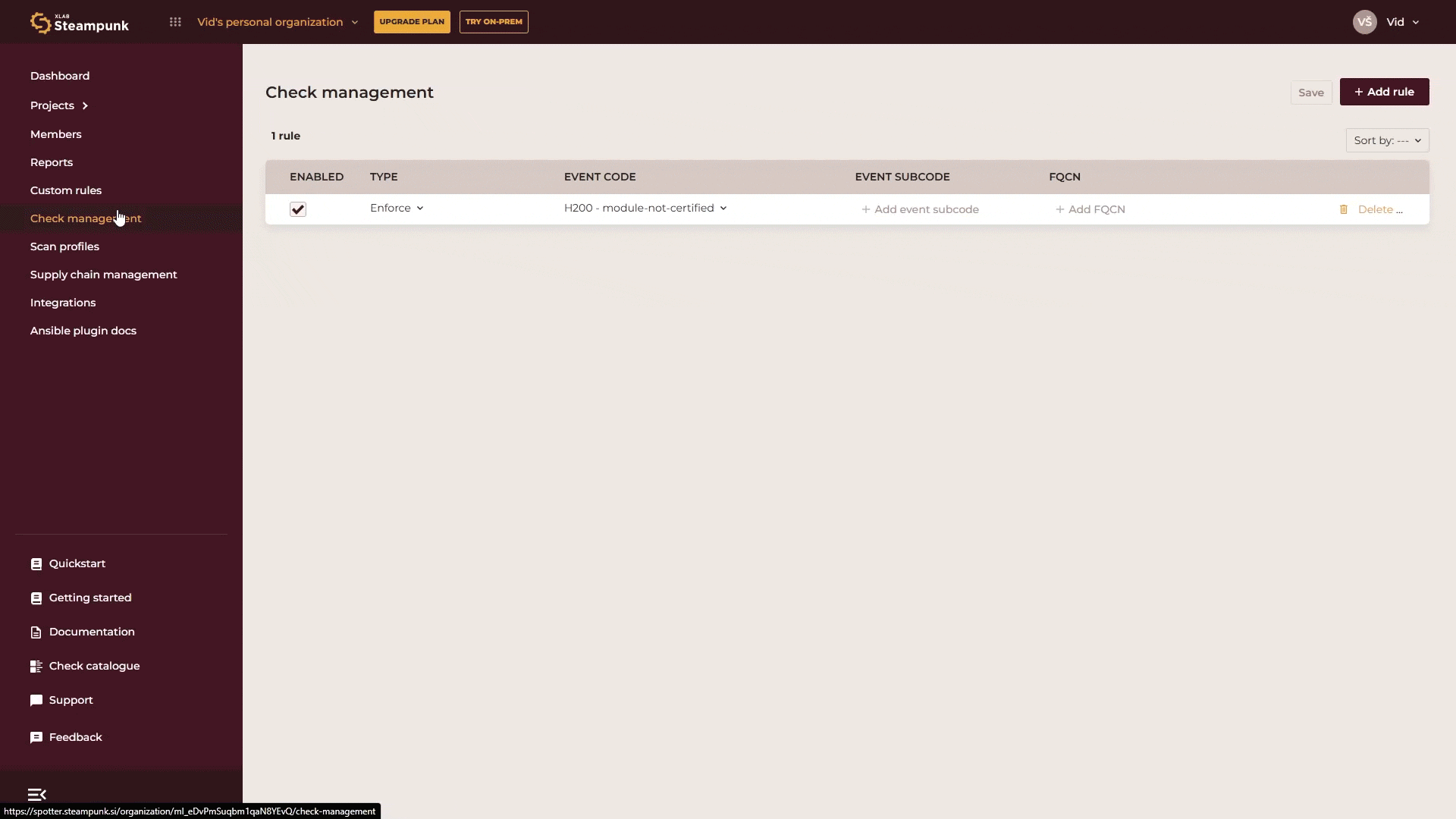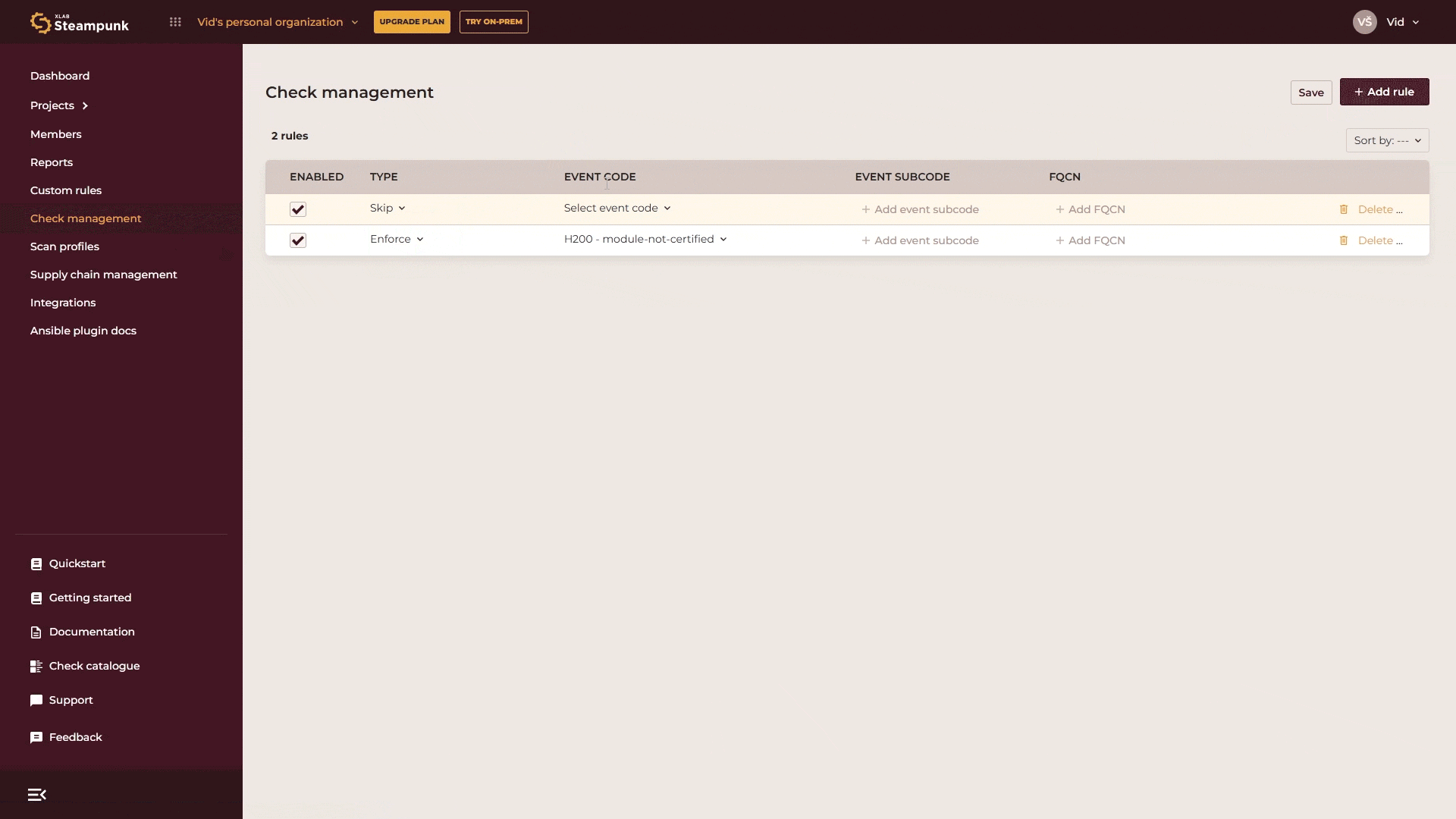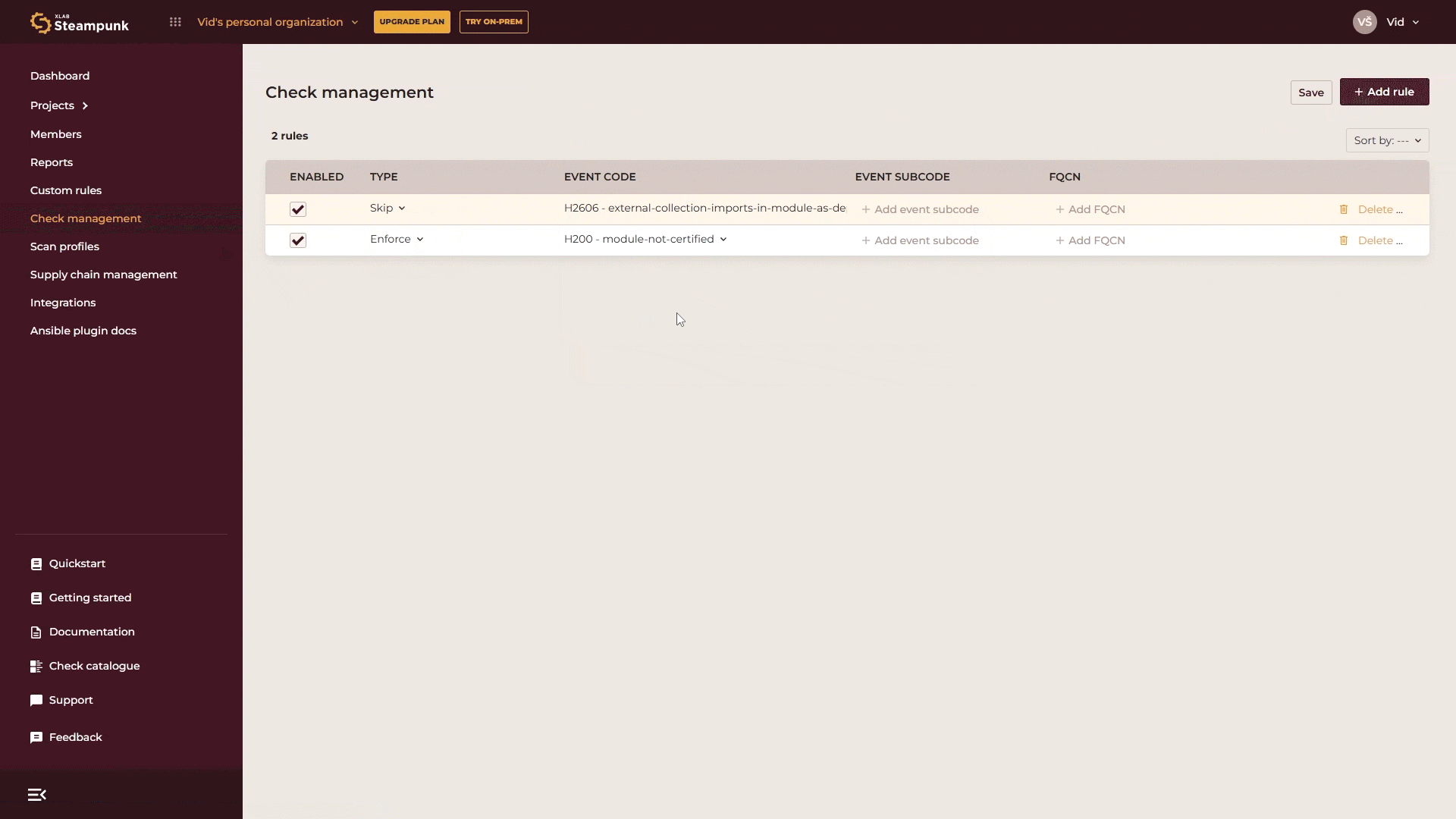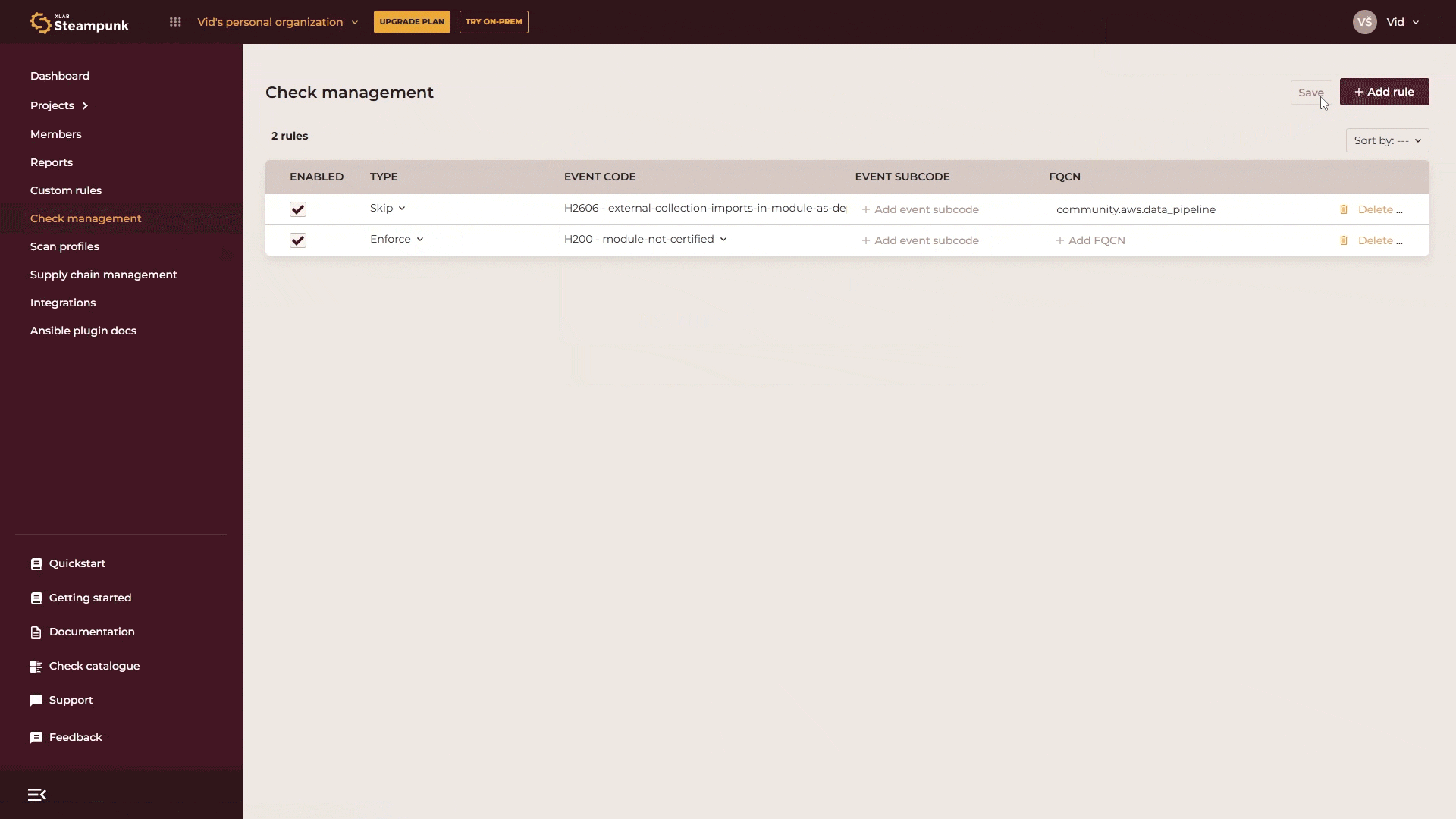
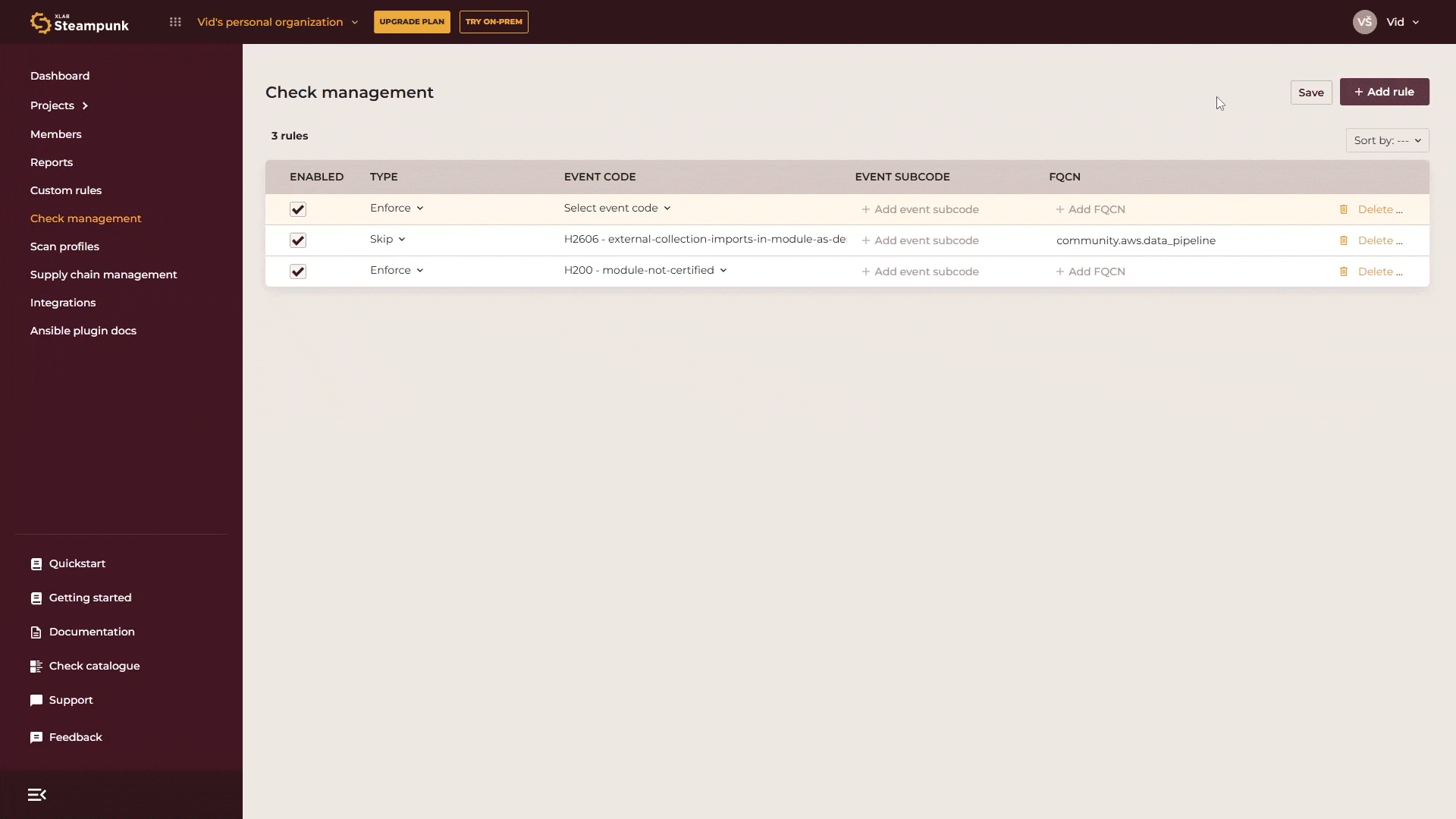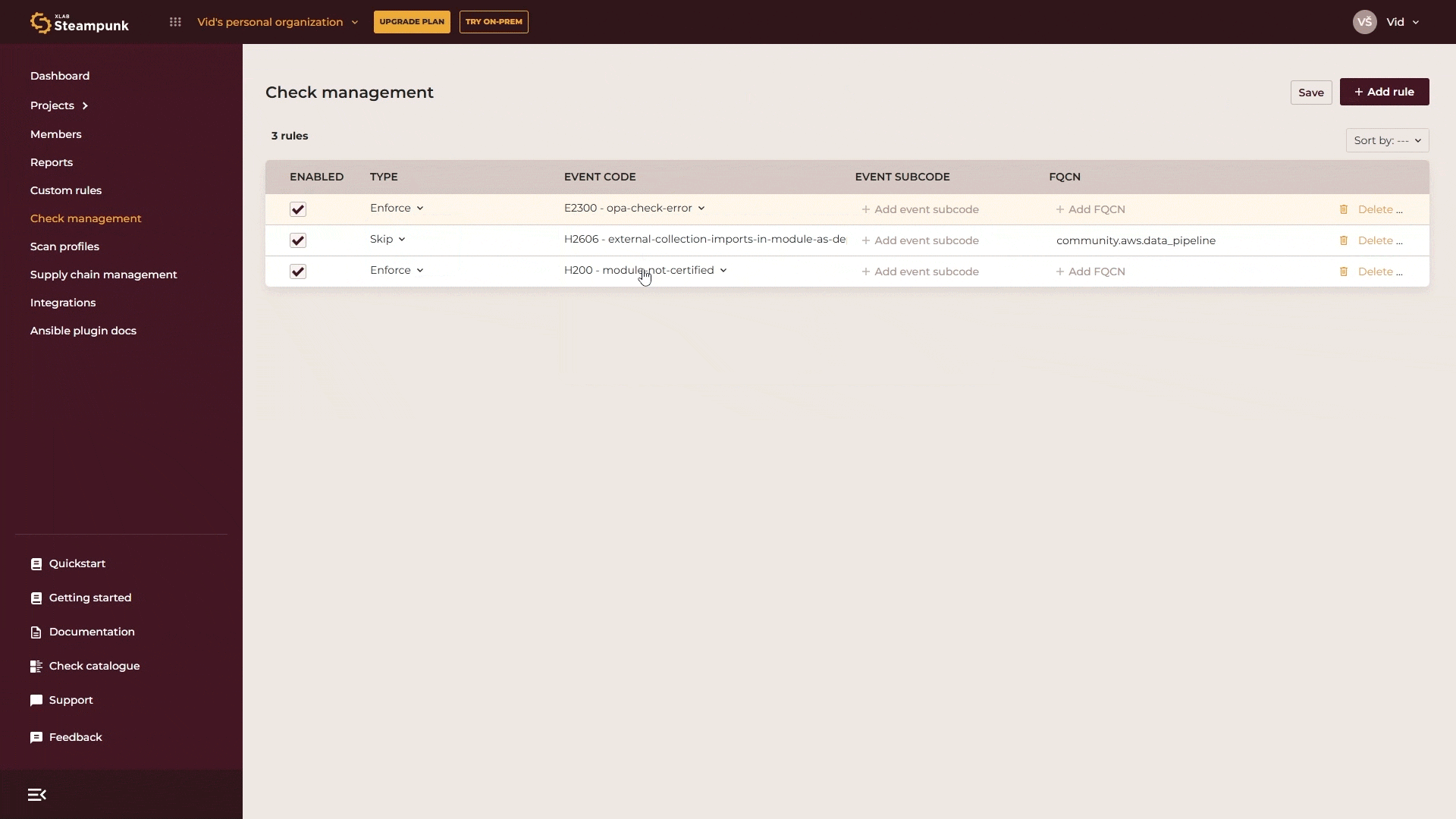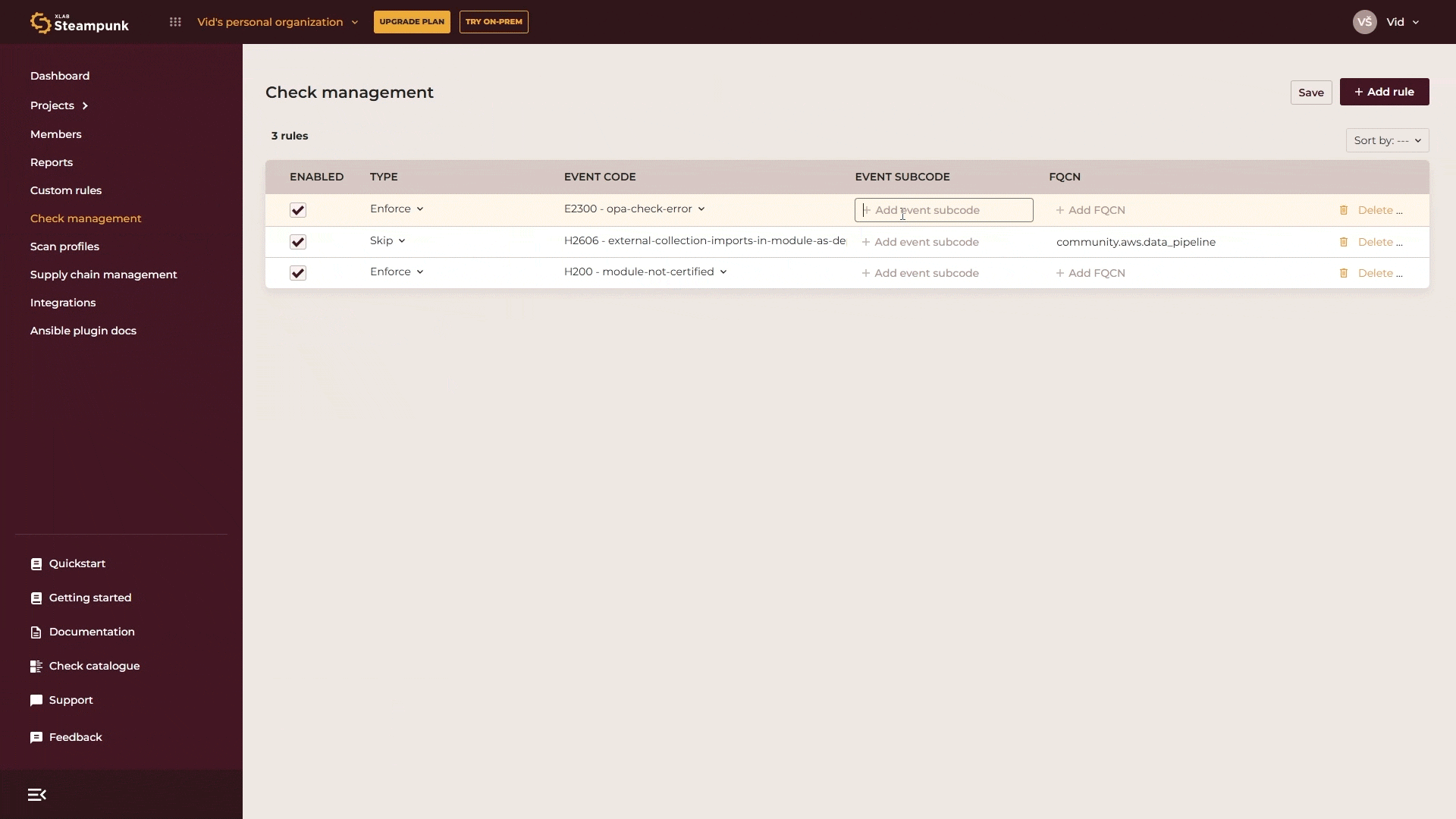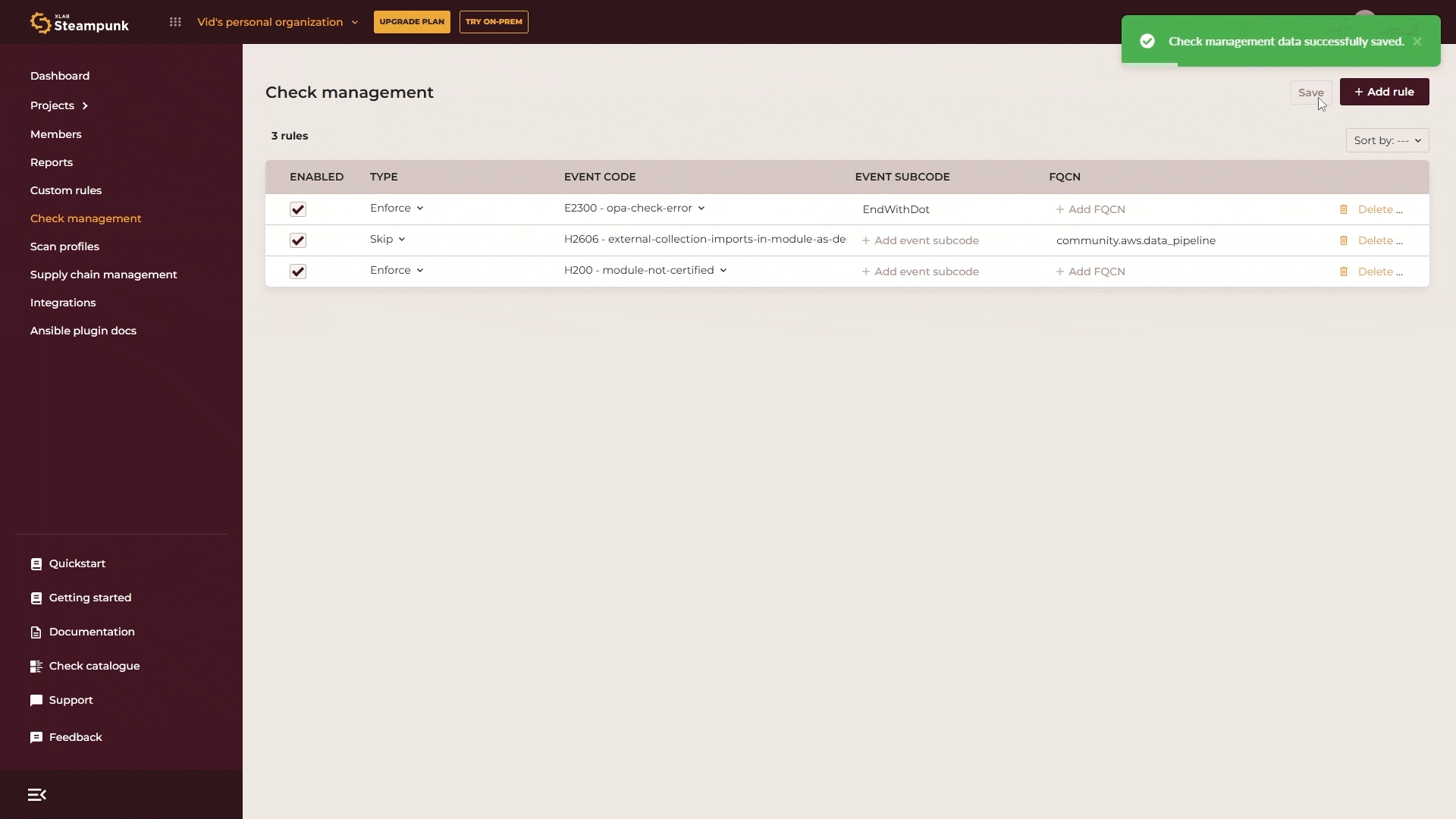
Organization admins can enforce or skip checks organization-wide with just a few clicks in the Spotter App. Any checks enforced at this level can’t be ignored when scanning by any user in your organization. Go to Check management, click Add rule, select whether you want to skip or enforce the check, enter the check code or search for it by name, and click Save.


If you want to manage specific checks without knowing their code or name, or want to explore the checks supported by Spotter, go to the Check catalogue. There you’ll find a detailed list of all available checks. Use the search function and enter relevant keywords.

Skip or Enforce Checks on Specific Module
If you want to skip or enforce a rule for a specific module, enter the Fully Qualified Collection Name (FQCN) for the module.

Enforcing Custom Rules
You can also enforce your custom rules, such as security or compliance checks. To find them, search for “OPA” (as custom rules are based on Open Policy Agent) or use the check codes 2300–2308. For example, to enforce a rule at error level, select E2300, specify the exact custom rule with its subcode from the list of custom rules and then save your changes. And that’s it, all rules are immediately applied and checked in all scans of all users in your organization.

Applying Rules cia CLI
Alternatively, you can also apply these rules on the organization level using the CLI by uploading a JSON or YAML file. Use the config set command to upload it and config clear to clear it.
Sample of an org-config.json file:
{
"skip_checks": [
{
"event": "W003",
"fqcn": "ansible.builtin.uri"
}
],
"enforce_checks": [
{
"event": "E005",
"fqcn": "community.crypto.x509_certificate"
}
]
}
spotter config set org-config.json
Copied!spotter config clear
Copied!Interested in the current settings for a specific organization? Simply use the config get command to see the current setup:
spotter config get
Copied!Scan level
Users working on solo projects can skip or enforce checks on the scan level through a configuration file or using switches.
Via the configuration file
As in the Spotter App, you can add FQCN if you want to skip or enforce a rule for a specific module, or you can add a subcode to identify specific custom rules that you want to set rules for. To enforce or skip checks via configuration file, create a file called .spotter.yml that needs to reside in the current project where your playbook is. And that’s it, the rules will be automatically applied.
The config file should look like this:
skip_checks:
- event: W003
fqcn: ansible.builtin.uri
- event: E601
fqcn: community.crypto.x509_certificate
enforce_checks:
- event: E005
- event: E903
Via Switches
When scanning, you can use the --skip-checks or --enforce-checks switches to specify which checks you want to skip or enforce. List the checks to be skipped by their IDs: and optionally also their FQCNs and subcodes, for example:
spotter scan --skip-checks E1300,E1301,H1302 playbook.yml
Copied!spotter scan --skip-checksW2600[subevent_code=B324],
H1900[fqcn=community.aws.data_pipeline] playbook.yml
Copied!Task-level Rules
Users can also skip checks on a task level, but they can’t enforce them. Simply add # noqa YAML comments at the end of the task line; or # noqa: event[fqcn=<fqcn>, subevent_code=<subevent_code>] if you want to skip checks for a specific module or custom rule.
---
- name: Sample playbook with comments
hosts: localhost
tasks:
- name: Get tpayload from the API # noqa: W003, E903
uri:
url:some-url"
method: GET
user: "username1"
- name: Ensure that the server certificate belongs to the specified
private key
community.crypto.x509_certificate: # noqa: E601[fqcn=community.crypto.
x509_certificate]
path: "{{ config_path }}/certificates/server.crt"
privatekey_path: "{{ config_path }}/certificates/server.key"
provider: assertonly
Learn more about check management in the Spotter docs.


