Set Scan Profiles
When conducting scans, we target specific goals. For instance, one project might focus on upgrading our Ansible environment to a newer
version, while another could aim to enhance playbooks for the current version. This means that certain check results provided by
Steampunk Spotter may be relevant for one project but not the other. Spotter addresses this by allowing the use of scan profiles via
the --profile argument - a selected set of checks. Make sure to add suitable arguments to your commands to make your scanning
experience optimal.
Whether you want to refine your playbook, upgrade it, or ensure its secure execution, the scan profiles ensure that the results align with your specific objectives. Watch DEMO or read blog to learn more about using scanning profiles.
Spotter currently supports the following profiles:
Default profile (--profile default)
This profile is suitable for day-to-day testing and improving Ansible Playbooks. It includes best practices, validation, and basic security checks but excludes upgrade and advanced security checks. For example, this includes check for the use of FQCN, module redirections and deprecation warnings, requirements collection version mismatches, best practice hints and a lot more.
If you run a general scan without specifying profiles, this is the profile that will execute.
Full profile (--profile full)
This profile displays the full range of check results included in the default profile and also includes advanced security checks and upgrade-related checks that will be especially useful during Ansible upgrades as they will help you update your playbook to work at a newer version. For example, you can see the default parameter value changes between module versions or check relevant for migration to the Ansible Automation Platform and execution environments.
spotter scan --profile full playbook.yml
Copied!Security profile (--profile security)
This profile includes advanced checks for potential security issues for when you need to focus only on secure execution of your playbooks, which is a full proof way of keeping your playbooks secure and reliable.spotter scan --profile security playbook.yml
Copied!Hint
In the Spotter App, you can view a detailed list of all checks included in each predefined Check Profile, along with their descriptions.Custom profile (--profile name)
You can create your own set of checks tailored to specific environments, projects, and needs with just a few clicks. Here’s how:
- Create a Profile: In the Spotter app, click “Create new profile” and choose the checks you want to include.
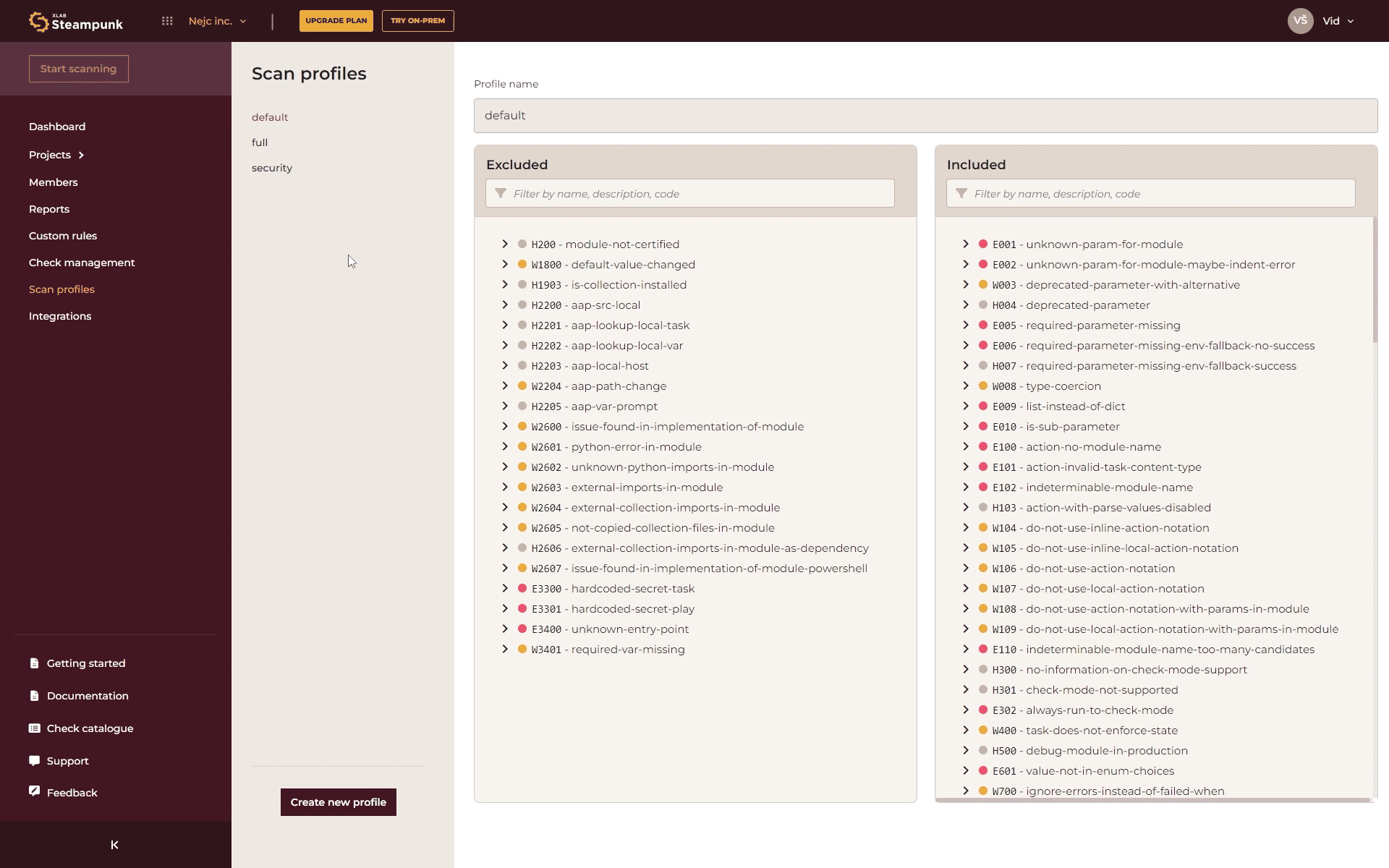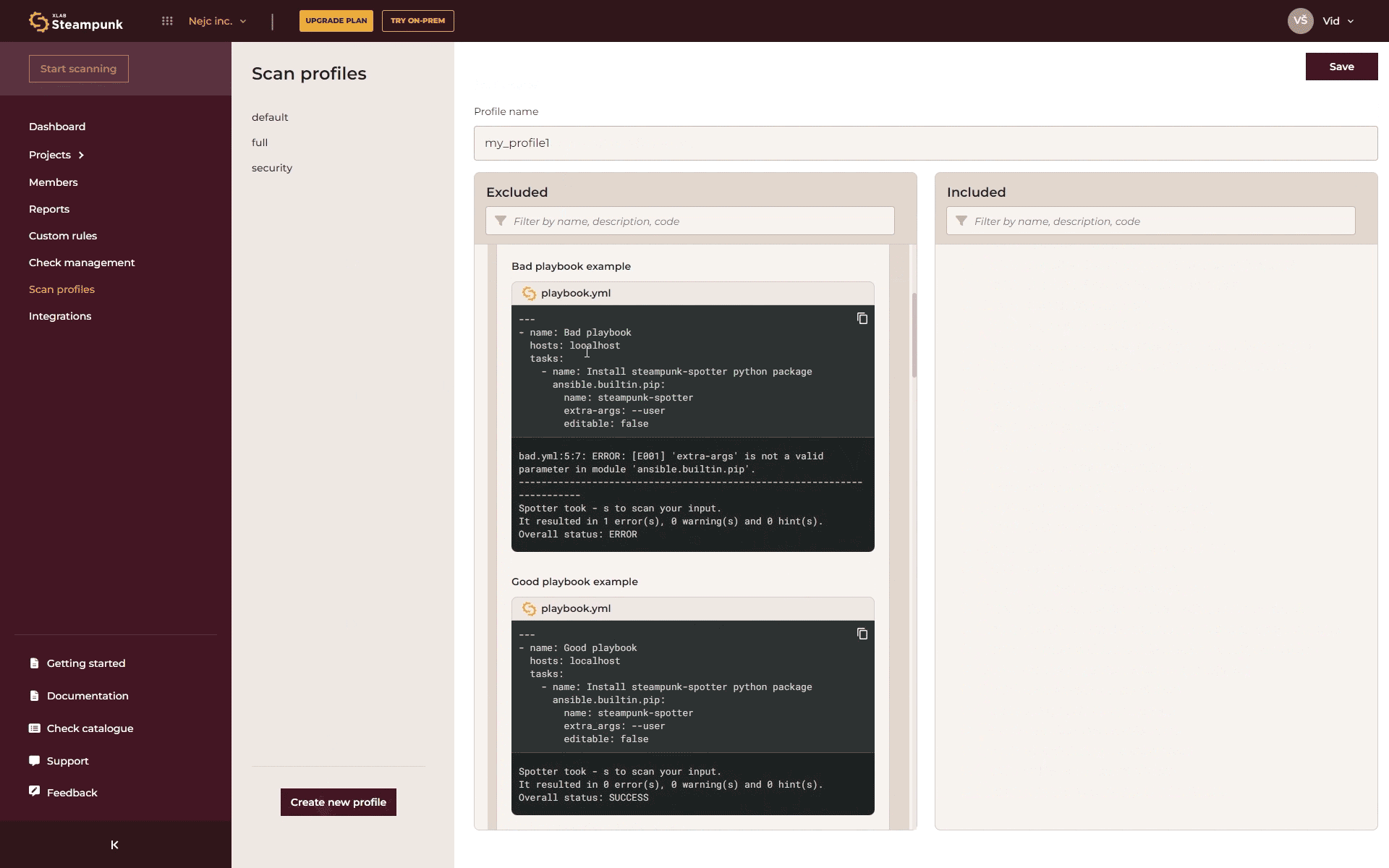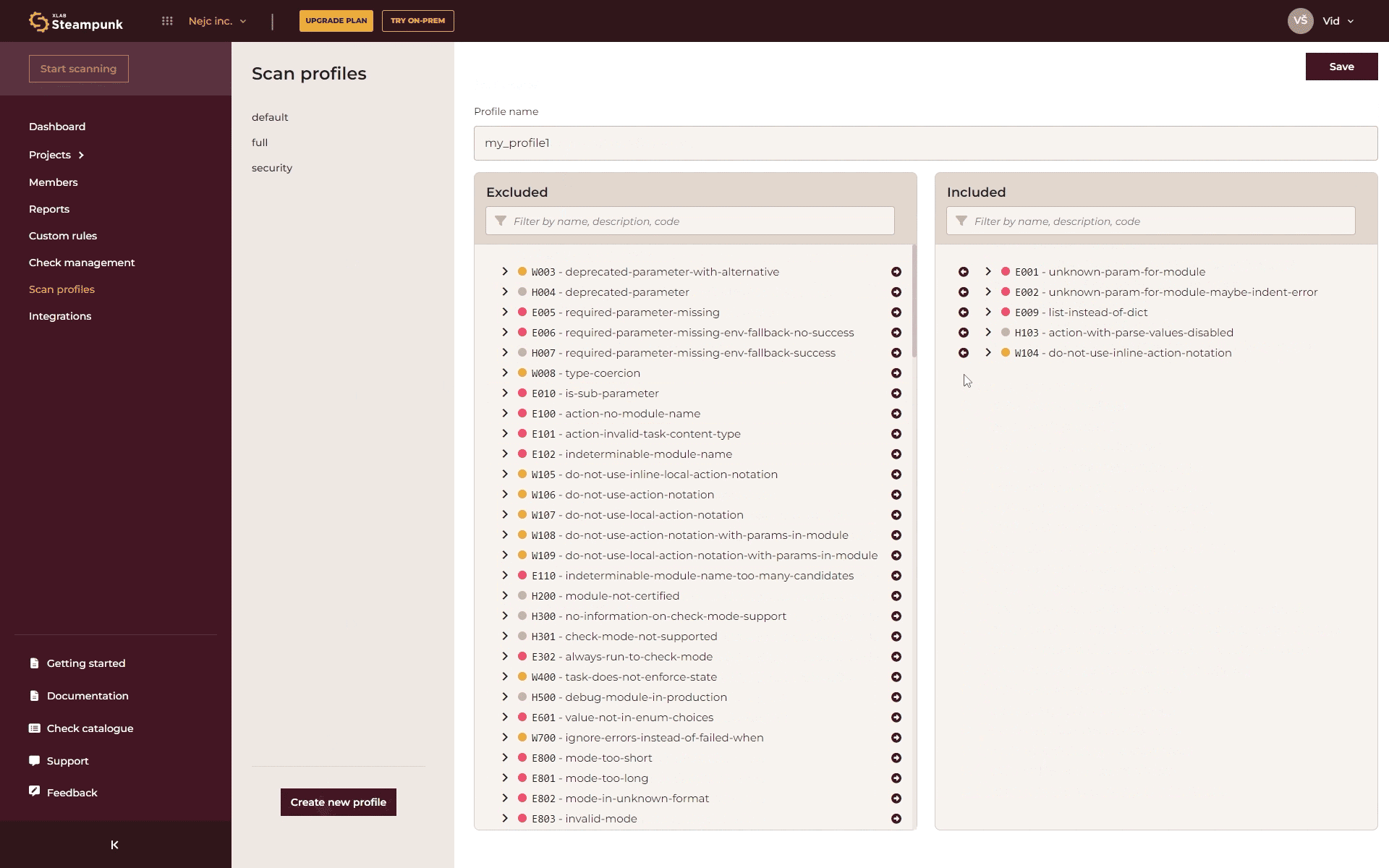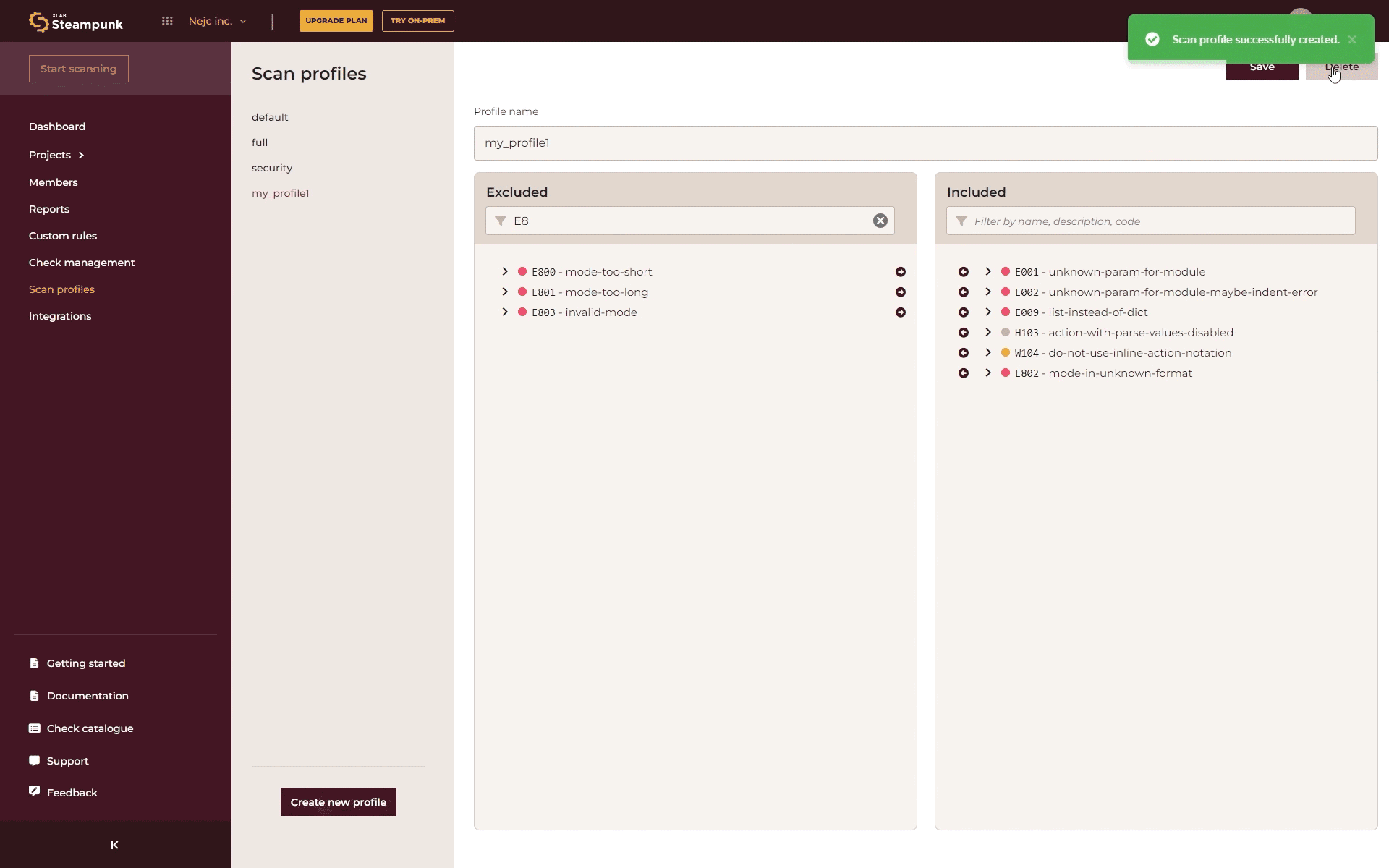

- Use the Profile: Use the following command (replace ’name’ with your profile name) in the CLI:
spotter scan --profile 'name' playbook.yml
Copied!

