Steampunk Spotter
Securing your automation: A guide to ensuring Ansible Playbook security
February 6, 2024 - Words by The Spotter Team - 9 min read
In IT infrastructure management, automation tools like Ansible have become indispensable for streamlining workflows, reducing errors, and increasing efficiency. But, as you know, with great power comes great responsibility. In the world of automation, that means taking care of the security side of things, especially when it comes to the playbooks that make the magic happen. See how to ensure implementation of secure playbooks and enhance the overall security of your automation workflows.
Risks of Non-Secure Playbooks
Using non-secure Ansible Playbooks in a business environment can pose various risks, potentially compromising the security, stability, and integrity of the IT infrastructure and the business as a whole. Non-secure playbooks can expose sensitive information, lead to data breaches, misconfigurations, security vulnerabilities, loss of control, and compliance violations (Learn more about ensuring compliance), potentially causing financial losses, disruptions in business operations, downtime, reputational damage, and loss of clients.

How to ensure your playbooks are secure?
As we’ve seen, security is not to be taken lightly, as non-secure playbooks have dire consequences for the whole business. So how to make sure your playbooks are secure, especially when dealing with hundreds or thousands of playbooks? Sounds impossible but let us put your mind at ease. When using Ansible Playbook platforms like Steampunk Spotter, offering full control over playbooks, assuring their security is a breeze.
Let’s take a look at the steps you should take to ensure playbook security and how Spotter can help simplify them.
1. Conduct in-depth playbook analysis
Everyone dealing with playbooks knows looks can be deceiving. Just because a playbook looks okay at first glance, that doesn’t mean it’s safe to run. So, what now?
You have two options. You can employ Ansible, Python and security experts to thoroughly examine each and every playbook to see if it’s safe to run or choose an easier way: playbook scanning tools doing the hard work for you in seconds.
Let’s take this playbook for example.
---
- name: Bad playbook
hosts: localhost
tasks:
- name: Create an example.com A record with value 127.0.0.1
inwx.collection.dns:
domain: example.com
type: A
value: 127.0.0.1
username: test_user
password: test_password
- name: Get current configuration for interface Ethernet2
community.network.cv_server_provision:
host: cvp_node
username: cvp_user
password: cvp_pass
protocol: https
server_name: new_server
switch_name: eos_switch_1
switch_port: 2
template: template_file.j2
action: show
- name: Create a new database with name "test_db"
community.postgresql.postgresql_db:
name: test_db
- name: Wait a maximum of 300 seconds specified tenant to be in the provisioned state.
f5networks.f5_bigip.velos_tenant_wait:
name: bigip_tenant1
state: provisioned
timeout: 300
- name: Ensure machines of which remote target address is 48 and 50 are powered off
community.general.ipmi_power:
name: test.testdomain.com
user: admin
password: password
state: 'off'
machine:
- targetAddress: 48
- targetAddress: 50
- name: Create a cloudformation stack
amazon.aws.cloudformation:
stack_name: "ansible-cloudformation"
state: "present"
region: "us-east-1"
disable_rollback: true
template: "files/cloudformation-example.json"
template_parameters:
KeyName: "jmartin"
DiskType: "ephemeral"
InstanceType: "m1.small"
ClusterSize: 3
tags:
Stack: "ansible-cloudformation"
- name: Create AWS data pipeline
community.aws.data_pipeline:
name: test-dp
region: us-west-2
objects: "{{pipelineObjects}}"
parameters: "{{pipelineParameters}}"
values: "{{pipelineValues}}"
tags:
key1: val1
key2: val2
state: present
It looks good, even basic scanning confirms that it’s aligned with Ansible best practices, so it will execute without any errors. But does that make it safe? No, not at all. So how to make sure it becomes safe?
By leveraging Ansible Playbook platform like Steampunk Spotter, offering in-depth playbook analysis, ranging from best practice to deep security checks.
So if we run Spotter’s Security profile, we see all the hidden potential issues.
> spotter scan --profile security playbook.yml Scanning...success. ━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━ 100% 0:00:00 Check results: playbook.yml:6:7: WARNING: [W2600::B411] Issue found in the Python implementation of module inwx.collection.dns: Using xmlrpclib to parse untrusted XML data is known to be vulnerable to XML attacks. Use defused.xmlrpc.monkey_patch() function to monkey-patch xmlrpclib and mitigate XML vulnerabilities. playbook.yml:14:7: WARNING: [W2600::B701] Issue found in the Python implementation of module community.network.cv_server_provision: By default, jinja2 sets autoescape to False. Consider using autoescape=True or use the select_autoescape function to mitigate XSS vulnerabilities. playbook.yml:26:7: WARNING: [W2600::B602] Issue found in the Python implementation of module community.postgresql.postgresql_db: subprocess call with shell=True identified, security issue. playbook.yml:30:7: WARNING: [W2600::B507] Issue found in the Python implementation of module f5networks.f5_bigip.velos_tenant_wait: Paramiko call with policy set to automatically trust the unknown host key. playbook.yml:36:7: WARNING: [W2600::B415] Issue found in the Python implementation of module community.general.ipmi_power: An IPMI-related module is being imported. IPMI is considered insecure. Use an encrypted protocol. playbook.yml:46:7: WARNING: [W2600::B324] Issue found in the Python implementation of module amazon.aws.cloudformation: Use of weak SHA1 hash for security. Consider usedforsecurity=False. playbook.yml:61:7: WARNING: [W2600::B324] Issue found in the Python implementation of module community.aws.data_pipeline: Use of weak MD5 hash for security. Consider usedforsecurity=False. Scan summary: Spotter took 1.012 s to scan your input. It resulted in 0 error(s), 7 warning(s) and 0 hint(s). Can rewrite 0 file(s) with 0 change(s). Overall status: WARNING Visit https://spotter.steampunk.si/organization/rB6YVxEKT_ehbEgLeVSlZQ/projects/Y3NfvNDQRCqEzfUZxnrbVg/scans/hju1tUjBT_6PjLymmvcrmg/ to view this scan result. >
Spotter security checks
To produce efficient, reliable and secure playbooks, playbook writers and security teams must join forces. Steampunk Spotter makes the job a lot easier for both, as it optimizes, speeds up and enforces security and efficiency of the whole automation workflow.
Using Spotter eases the burden on both Ansible Playbook writers and security teams and helps businesses secure their playbooks and managed infrastructure.
Learn more about ensuring security and compliance with Spotter.
Steampunk Spotter includes built-in checks of three main types:
- Security Checks and Best Practices for Major Clouds
These checks verify potential misconfigurations of cloud resources based on the common best practices for major cloud providers such as Azure and AWS and allow Ansible Playbook writers to focus on describing the necessary cloud resources without requiring a comprehensive understanding of security best practices, as Spotter will warn you if you are provisioning and configuring resources in an insecure manner.
- Checks for Security Issues in Ansible Module Implementation
Spotter consistently scans all Ansible modules (both built-ins and modules from external collections) to detect security issues within them. If a module with such issues is used in scanned Ansible Playbooks, the user is warned of a potential risk.
- Checks for Security Issues in Dependent Python Packages
Spotter checks the third-party dependencies of Ansible modules. It checks for potential issues and considers publicly available CVEs (Common Vulnerabilities and Exposures) to ensure the security team is aware of these dependencies and potential threats before applying Ansible Playbooks.

2. Ensure secure modules are used in playbooks
Modules are core building blocks of Ansible Playbooks as they are the ones that execute a task. Luckily, you don’t have to come up with them on your own, there are many different modules available, covering a wide range of tasks, and you can find them on Ansible Galaxy or Automation Hub. But unfortunately, there’s no way of telling if the examples are actually of high-quality. They might have foregone additional syntax checks, but that still doesn’t guarantee that they will do what they’re supposed to do, or if they are actually safe to use in your environment.
To determine their quality, one has to be a Python expert, but the great thing about Ansible is it’s written in human-readable language and therefore you don’t actually need programming language knowledge to write them. So how do you check if the modules are safe to use?
Before using the chosen module in your playbook, head over to the Steampunk Ansible Collections Documentation. It’s a comprehensive repository of all versions of all Ansible Collections available on Ansible Galaxy, generated by XLAB Steampunk team of Ansible experts. Not only can you easily browse all versions of all collections in one place, but each example is verified with Steampunk Spotter so you can instantly see its quality and decide if it’s safe to use in your playbooks.
And, of course, to be safe you’ve then applied them correctly, scan finished playbook with Spotter. Better safe than sorry, right?
3. Bulletproof your security: Enforce or skip checks organization-wide
Even when playbook scanning tools warn of security issues, developers may choose to overlook them, either to save time or because they don’t recognize the full extent of their impact. Spotter’s Enforce check feature prevents security concerns from being overlooked. Organizations can set checks to always be enforced or skipped, depending on their security requirements.
High-risk issues can be enforced for all scans, resulting in an error if a playbook includes a task using the associated module. This can be further configured in the CI/CD pipeline to prevent such playbooks from being merged until the issue is resolved.
Low-risk issues can be skipped from all scans, preventing users from being prompted to address them for the specific module.
Scan customization can also be applied to an Ansible project or even a single Ansible task.
By selectively enforcing or skipping checks using Steampunk Spotter, you can strike a balance between security and usability, ensuring that your playbooks are secure without sacrificing functionality or performance.
4. Enforce security by adding Custom rules
Ansible security best practices are a crucial foundation, but what about your organization’s unique security requirements? With Spotter’s Custom rules feature, you can seamlessly integrate your specific security policies into the scanning process. This means that Spotter doesn’t just evaluate compliance with general best practices and security standards; it also checks against your own proprietary rules. And the best part is, Spotter uses a universal OPA framework and human-readable Rego language, making it accessible to both technical and non-technical users.
5. Regular monitoring – integrate playbook scanning tools in CI/CD
Even if playbooks are initially secure, it’s crucial to continuously monitor them to ensure they remain that way. Spotter continuously scans and alerts you of any security issues or changes that could impact the integrity of your playbooks. For service providers, regular daily monitoring is essential for providing reliable and secure services to clients. Schedule automatic nightly CI runs with Spotter to identify and rectify any issues quickly, preventing them from accumulating and causing major disruptions. Spotter also tracks the performance of your playbooks over time to detect trends and anomalies.
6. Efficiently manage playbooks
Effectively managing playbooks requires a centralized platform that unites scan results, providing a comprehensive overview of your Ansible infrastructure’s health.
Spotter’s Dashboard acts as a centralized control panel for monitoring and managing playbook performance, security, and compliance. It provides a clear view of your playbook landscape, helping you identify and prioritize critical issues for remediation.
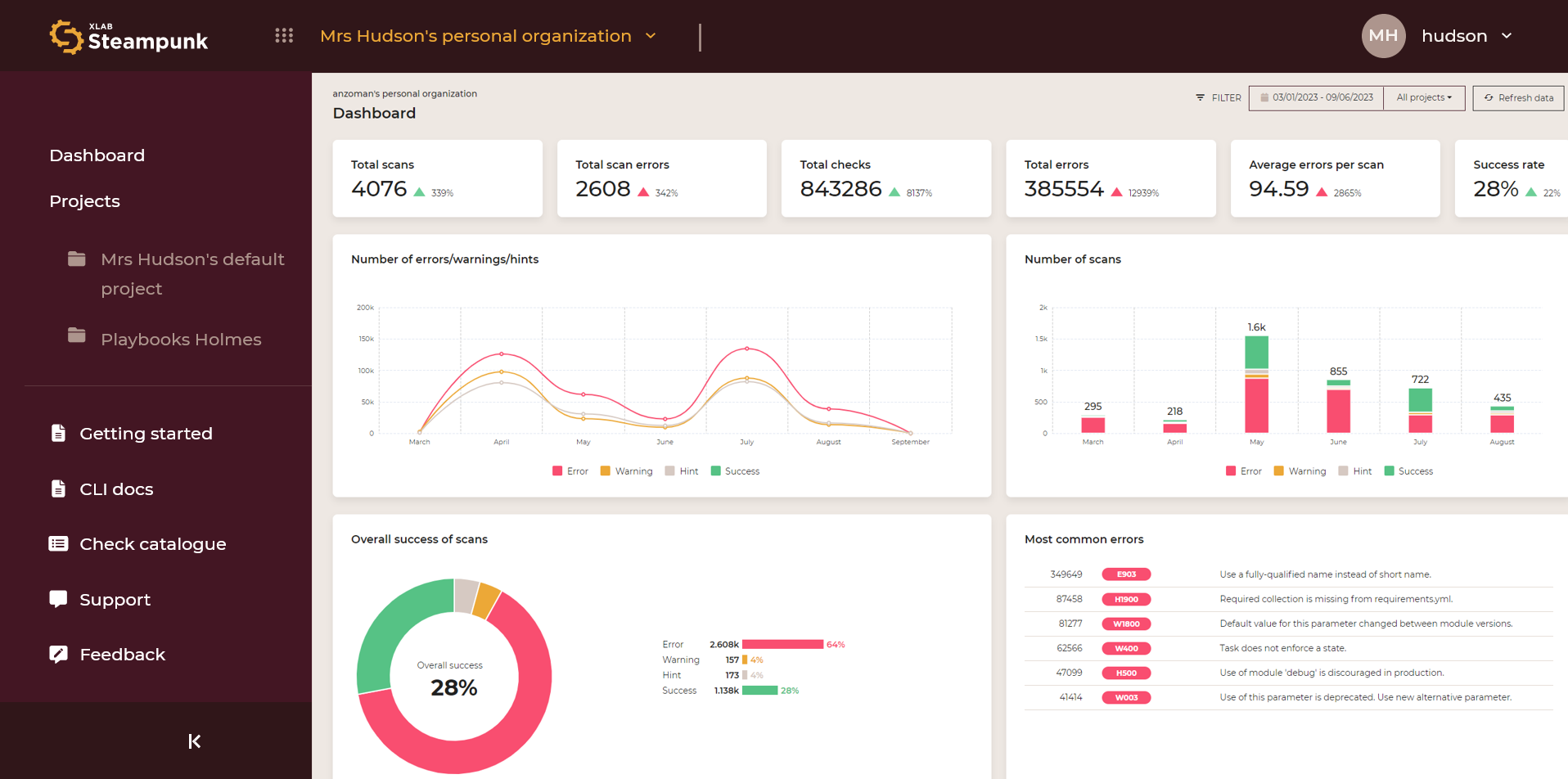

In addition to the Dashboard, Spotter also generates comprehensive reports on playbook conditions, highlighting potential areas for improvement and providing valuable insights. These reports are easily accessible and can be shared with relevant stakeholders, fostering collaboration and ensuring that everyone is on the same page regarding the status of playbooks.
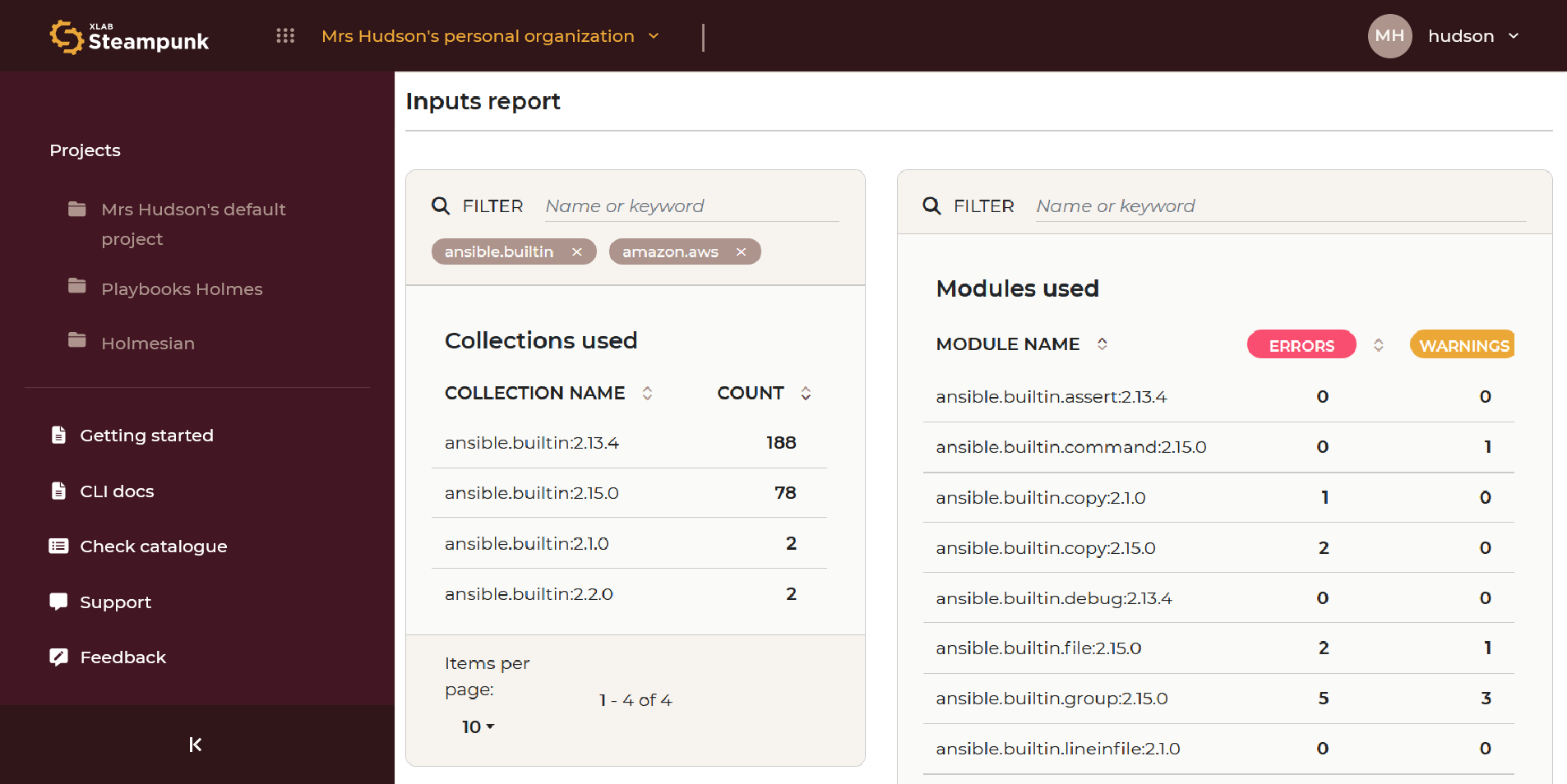

Spotter’s visibility and collaboration features empower team members to gain insights into the impact of their changes on the project’s validity, quality, and security. Developers can focus on the scanning results, while managers can optimize automation processes and enhance overall DevOps efficiency.
Watch this video to learn more about Spotter’s visibility and collaboration features.
Conclusion
Ensuring the security of your Ansible Playbooks is absolutely essential in safeguarding your IT infrastructure and business operations. With Steampunk Spotter at your disposal, you can proactively detect and resolve any security vulnerabilities, guaranteeing the reliability and integrity of your automation workflows. Take control of your Ansible automation with Steampunk Spotter - the indispensable platform for a secure DevOps lifecycle. Try it out today.


